Malicious script in Google and X stole $58m in crypto from over 63k users
The malicious Wallet Drainers script used phishing campaigns in Google search results and Twitter ads, stealing millions of dollars from users.
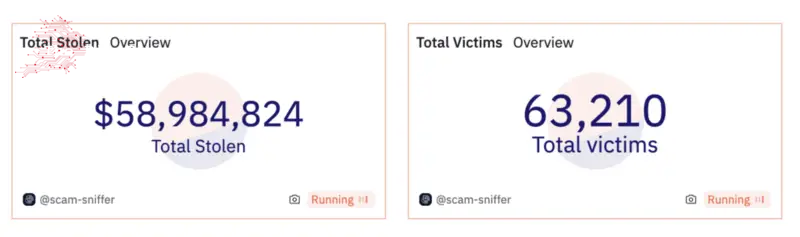
According to Scam Sniffer, the malicious script stole almost $59 million in digital assets from more than 63,000 victims over nine months. Over the past nine months, 10,072 websites have been linked to Wallet Drainers, with activity peaking in May, June and November.
Most of the advertisements were related to cryptocurrency and NFT airdrops. Moreover, some of them were references to popular blockchain projects, such as Ordinals Dogecoin (DOGE). Malicious ads used regional targeting and page-switching tactics to bypass ad audits, complicating the review process. A test of X’s ad in the feed showed that nine were phishing ads, with over 60% using this wallet drainer.
“Phishing ads employ redirect tricks to seem legit, like disguising links as official domains that actually lead to phishing sites.”
Scam Sniffer experts
Earlier this month, Ledger, a popular manufacturer of crypto hardware wallets, warned its customers about the dangers of using dapps. The reason was a discovered attack on the supply chain.
Attackers injected malicious javascript code into the Ledger dapp Connect Kit library, which allows web3 applications to interact with Ledger wallets. This code automatically stole cryptocurrency and NFTs from accounts connected to the service.
According to Chainalysis, the activity of attackers is beginning to increase – from May 2021 to December 2023, phishers stole $1 billion worth of cryptocurrency. At the initial stage, analysts identified at least 1,013 addresses involved in targeted phishing. Phishing refers to a scam in which the criminal sends emails or SMS messages asking you to click a link or log into your account.
Comments
Post a Comment